Data Center Operations & Customer Configuration
📌 The instructions in this manual apply only to customers using standard TLS connections to Retarus.
If you use a VPN or MPLS connection, or the Advanced Routing & Rewriting functionality, contact Retarus for guidance on configuring your connection.
Retarus Email Security infrastructure
Emails sent from communication partners to the customer (inbound) are first processed within the Retarus Email Security infrastructure and then forwarded to the customer’s email systems.
Customers can also choose to send their emails directed to communication partners (outbound) to the Retarus Email Security platform for filtering and analysis, and let Retarus then forward the messages via the internet to the intended recipients.
Retarus focuses on providing the highest level of security, flexibility and availability for its cloud-based messaging services. In order to guarantee high availability of these services including failover and MX load balancing, Retarus operates geographically separated data centers and provides customers access to those facilities.
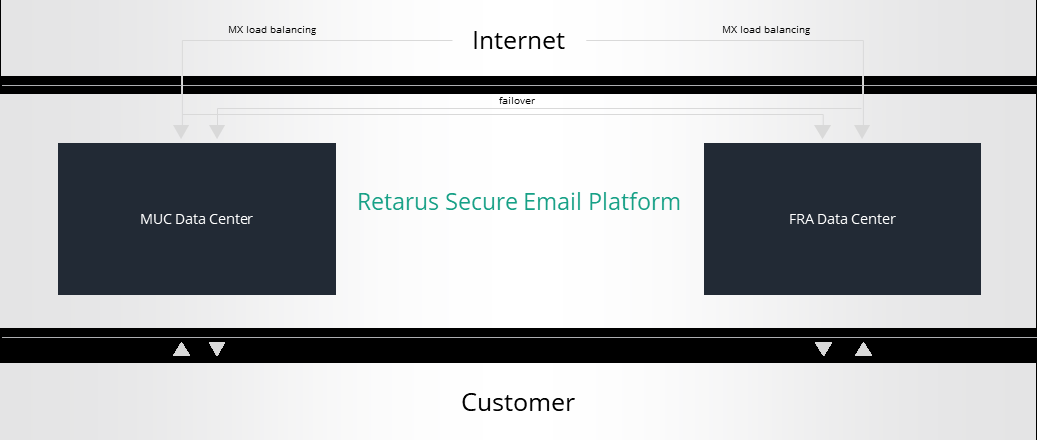
For Retarus Email Security, Retarus operates two data centers at the following locations:
Munich, Germany (primary, Retarus headquarters’ data center)
Frankfurt, Germany (peer data center)
The distance between these data centers is approximately 400 km (250 miles).
The data centers’ certifications include ISO22301, ISO27001 and PCI-DSS. Access to the data centers is monitored via camera surveillance and security guards. Multiple barriers ensure access is possible for authorized personnel only. All employees of Retarus, both active and retired, are bound to the privacy regulations stipulated in the EU General Data Protection Regulation (GDPR). Furthermore, the data centers are operated in accordance with the processes of the ITILv3 standard.
Data center operations in detail
Please find below a more detailed overview about the Retarus Email Security dual data center operations. (Not all customers use all features listed here.)
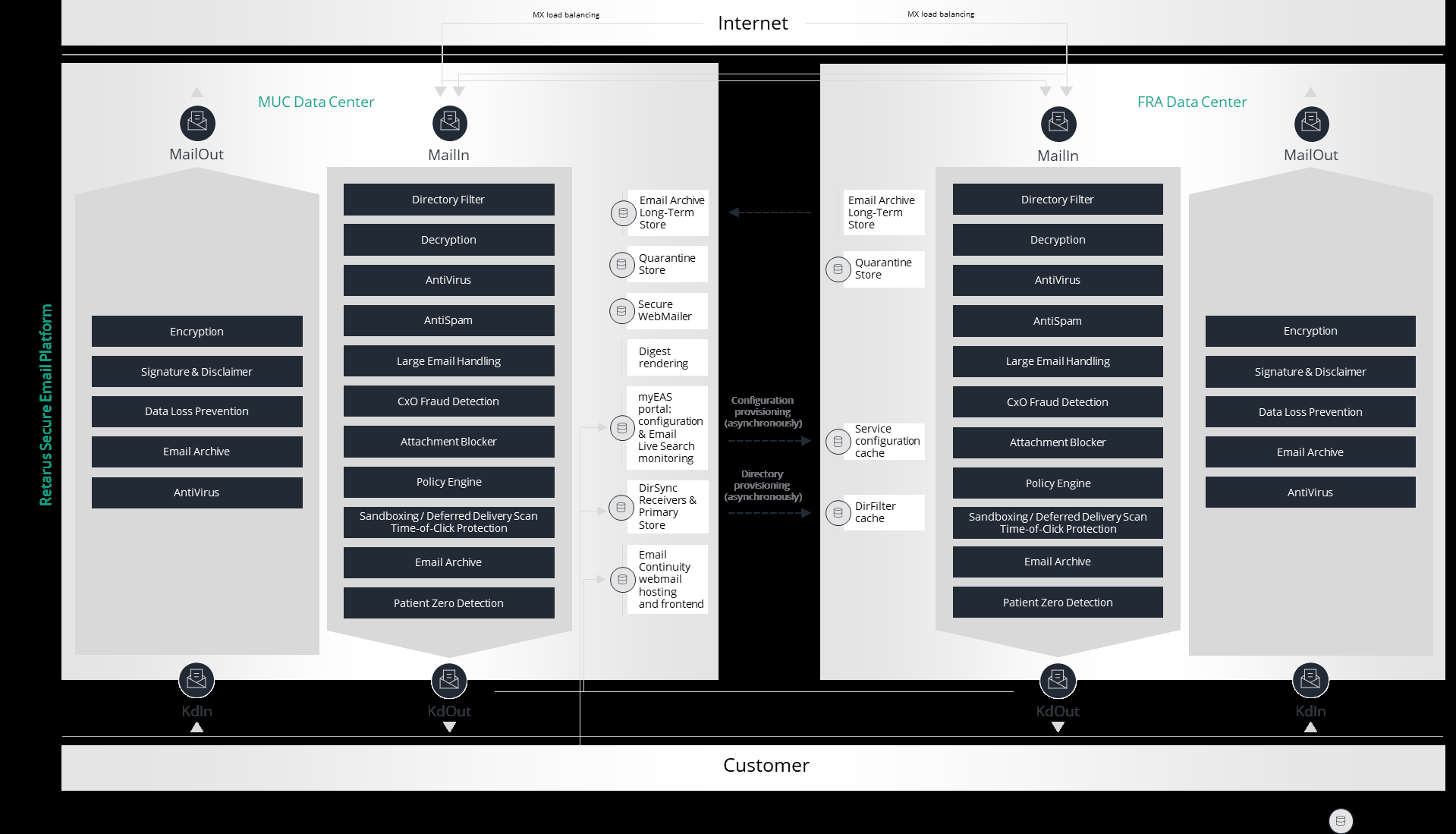
Infrastructure operations restrictions
For regular email processing, both data centers provide the full feature and functionality set of the Retarus Managed Email Security Services, and thus can operate independently from one another. However, due to the architecture of the solution, some infrastructure components are only located in the Munich data center. They serve as either a primary system there, distributing information to the peer in Frankfurt, or as a solitary system:
Enterprise Administration Services (EAS/myEAS) and configuration store
The EAS portal is a solitary system operated in the Munich data center only. Any settings and configuration changes completed in the EAS (profile settings, AntiSpam rules, block- and allowlists etc.) are stored in the configuration settings primary store in Munich, from where they are propagated to all production sites. Quarantine releases are only possible as long as the Munich data center is available.Email Live Search and reporting
Both Email Live Search and reporting are operated in the Munich data center only. All production facilities forward required Email Live Search and reporting information (tracking points etc.) to the appropriate stores in the Munich datacenter where it can be accessed via the myEAS portal.Email quarantine and digest (“Email Security Report”)
The email quarantine is available in both data centers. Quarantined emails are stored either in the MUC or FRA data center, the index is synchronized between both data centers. Digest rendering is operated in the Munich data center only.DirSync and Directory Filter (“DirFilter”)
The DirSync Receivers are solitary systems available in the Munich data center only. The DirFilter primary store is operated in the data center in Munich, propagating all email address and alias address information to all production facilities at regular intervals.Email Encryption incl. Secure WebMailer
All Secure WebMailer systems for customers are operated in the Munich data center only which serves as receiver for the other data centers.Email Archive
The Email Archive is working in both data centers. The primary store in the Munich datacenter receives and stores all messages, whereas the secondary store in Frankfurt queues and pushes all messages to be archived to the Munich store at regular intervals.
Customer configuration
To be able to benefit from the distributed infrastructure, customers need to configure their systems and their MX records with the appropriate priorities in their DNS (using the predefined names specified by Retarus) as described below in this document. From Retarus, no special configurations are required.1
This applies only if TLS or plain SMTP is used for connecting customers to Retarus. If this connection is to be realized via VPN, dedicated line, or MPLS, the corresponding networking connectivity needs to be created between customers and Retarus.
Mandatory, indispensable configuration assistance
In most mail flow scenarios, customers can set up their connectivity with the Retarus data centers by themselves, i.e. by modifying or extending the settings in the EAS portal or by changing their MX records. Retarus advises connectivity tests before publishing any information such as MX records in the DNS.
However, if
customers use VPN or MPLS to protect the network communications,
or if no DirSync was yet set up for customers,
or if customers streamline direct message delivery to dedicated locations by Retarus Advanced Routing & Rewriting,
the assistance of Retarus implementation engineers to configure and test all configurations in close cooperation with the customer is required to warrant that all the service options and components are working as intended.
Configuration for email traffic from the internet to Retarus
When using the Retarus Email Security Services, Retarus acts as gateway between the Internet and your email server for incoming emails, so the MX record of your domains (to be configured via DNS) has to point to the Retarus data centers.
During the year 2023, we are introducing customer-individual MX records (instead of the general ones used by all customers so far) that point to both Retarus data centers in Munich and Frankfurt.
For features like DMARC validation, these individual MX records are already mandatory. In the future, all customers should use the new MX records. Dedicated MX records include a random number, e.g., "mx-26757099.mail.eu.retarus.com".
DNS configuration example for all your domains (MX record has to be replaced by your individual one):
@ IN MX 10 mx-26757099.mail.eu.retarus.comYour individual MX record can be found in the myEAS portal:
myEAS (https://myeas.retarus.com) - Administration - MX Record.
Retarus advises connectivity tests before publishing any information such as MX records in the DNS.
Configuration for outbound email traffic from the customer to Retarus
You will need to adjust your smart host configuration in your email servers to point to both Retarus outbound email relays. Retarus recommends to use the DNS settings from the table below for routing configuration, while the IP addresses should only be used for firewall configuration (if needed).
Retarus will accept messages at the following mail server (plain SMTP):
Processing domain | A record (round robin between DE1 and DE2) |
|---|---|
DE (Germany) | mx-out.eu.retarus.com |
This value may be subject to change in special configurations such as VPN, dedicated lines, MPLS, etc., and these special configurations require assistance from Retarus Implementation Engineers.
Depending on the capabilities of your smart host configuration, you may decide to set priorities for the Retarus relaying servers in Munich and Frankfurt. Retarus recommends balancing the systems equally.
Please keep in mind that Retarus needs to be informed about all the IPs that you try to relay emails from. You can either enter these IP addresses yourself in the EAS portal (https://eas.retarus.com) via
Administration - Email Security - Service Settings - General
into the table IP address(es), or you contact Retarus at support@retarus.com, requesting your IP address(es) to be permitted for relaying.
Configuration for email traffic from Retarus to the customer’s email servers
Retarus data centers will attempt to forward all messages processed for you to your email servers. Due to this, you will need to grant permission to the email servers of both Retarus data centers, Munich and Frankfurt, in your infrastructure to accept emails from Retarus for you. Depending on your infrastructure, this may require setup in your firewall(s), in your email server(s) or in both.
Retarus will try to send messages to you from the following IP addresses (mail servers):
IP Addresses |
|---|
185.236.172.47 Additionally needed for customers using Advanced Threat Protection (ATP): Additionally needed for customers using Advanced Routing & Rewriting: |
These values may be subject to change in special configurations such as VPN, dedicated lines, MPLS, Advanced Routing & Rewriting, etc., and these special configurations require assistance from Retarus Implementation Engineers.
The IP addresses listed above should also be included in your company-own Allowlist to make sure that the traffic reaches you under all circumstances.
SPF records
As for SPF records, you are recommended to include the Retarus default SPF record, which encompasses all IP addresses of Retarus reserved for outbound messaging. The default Retarus SPF record is published in the DNS as a TXT record of the domain:
_spf.retarus.com
In order to include this record, follow the SPF syntax required for this purpose. As an example, your DNS record could have a TXT record, which includes the Retarus SPF records, thus encompassing all email relays of Retarus, with the soft fail option:
v=spf1 include:_spf.retarus.com ~all