Secure Email Gateway Description
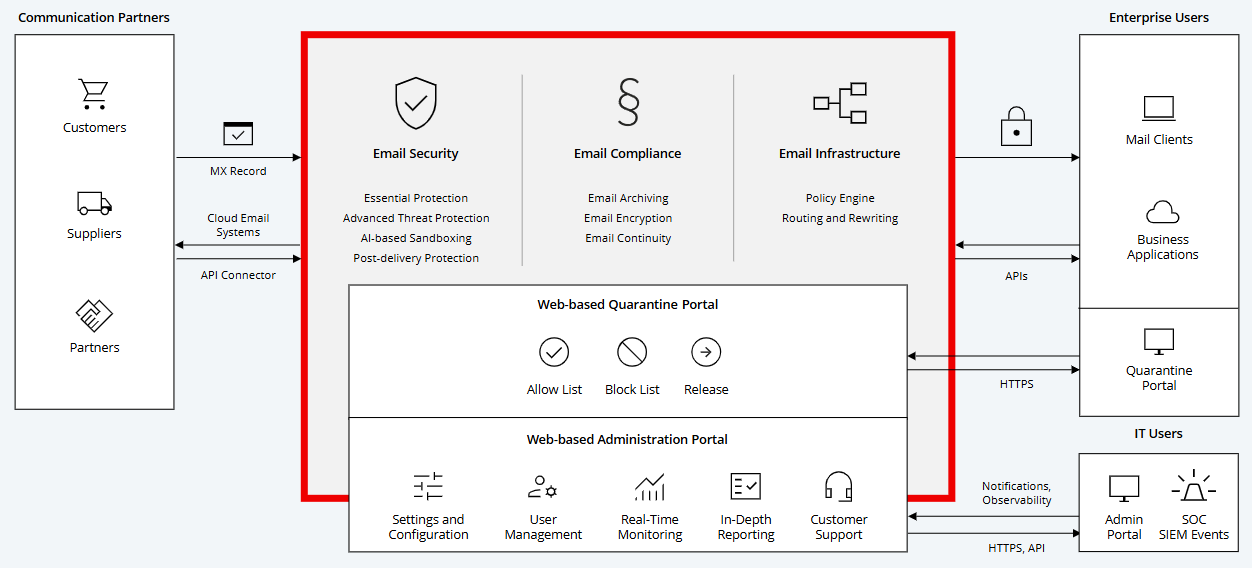
The Retarus Secure Email Platform combines comprehensive security (Advanced Threat Protection, a patented Postdelivery Protection, Sandboxing), enhanced email routing via the Predelivery Logic, with Email Archiving, Email Encryption and Email Continuity. Additionally, existing business applications can be connected to the platform via the Retarus Transactional Email modules. The range of services are structured into the following main product categories
Email Cloud Gateway
Email Security
Email Compliance
Email Infrastructure
System Architecture
Email Cloud Gateway
The Retarus Email Cloud Gateway offers foundational functionalities for managing and securing the SMTP message traffic. It can be used as a stand-alone service, but may also be expanded using additional modules of the Retarus Secure Email Platform.
The Email Cloud Gateway includes the following functionalities:
Directory Filter / Reputation Management
The Director Filter rejects those emails in a RFC-compliant way ('reject method') addressed to recipients not configured in the Retarus Enterprise Administration Services Portal (EAS Portal). This can be configured and updated either manually by the customer through the EAS Portal itself, or automatically through Directory-Synchronization in a format specified by Retarus with the customer's address books and directories.
The reputation of senders of incoming emails is checked via the Inbound Reputation Management which supplements the Directory Filter. A sender’s authorization is validated via the SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) mechanisms. In the event of failed validation of classified emails, such emails are handled in accordance with the Customer configuration in the EAS portal or - if activated by Customer - further processed pursuant to the DMARC policy specification (Domain-based Message Authentication, Reporting & Conformance) of the domain owner (sender) (actions: None, Quarantine, Reject).
Note: The use of DMARC requires routing to a dedicated MX record of Retarus.
AntiVirus Multiscan 2x
Retarus scans incoming and – where agreed – outgoing messages for viruses. To carry out these scans, Retarus uses two virus scanners of their choosing from different providers. As soon as there are updates or releases from these providers, Retarus will use them for virus scans immediately. Should a virus be detected, Retarus deletes any and all emails infected. The respective recipients of the infected emails and/or their administrators saved for such an occasion, will be informed as part of quarantine management.
DHA Protection
Directory Harvest Attack (DHA) protection for the email domain(s) selected by the domain owner. Messages to invalid recipients within the domain concerned will be rejected. The receipt of additional messages to invalid recipients will be restricted by throttling the identified sender of these messages.
Backscatter Protection
Protection from misuse of bounce messages automatically generated for sending (Backscatter).
Backscatter is unauthorized use of another person's valid email address for spam campaigns. It may be the case that the receiving email server of the recipients receives a large number of delivery status notifications (e. g. if the receiving address does not exist) at the valid email address of the person that was used as the sender without their knowledge. Emails are not delivered to the actual sender.
Thanks to Backscatter Protection, an increased number of these automatically-generated messages will be identified and filtered out, and their delivery will be prevented using isolation of the recipient concerned in personal quarantine. In personal quarantine, these messages will be marked as NDR Spam.
Email Back-up / Queuing
In case of undeliverability of the messages intended for the customer, Retarus will store the respective incoming messages for a maximum of 96 hours. Should the undeliverability not be able to be resolved, the sender of the message will receive a notice of undeliverability via email. Retarus will attempt delivery in regular short intervals throughout this span of 96 hours. Should undeliverability end within this time span, the incoming messages will be forwarded by Retarus in batches.
Large Email Handling
Retarus Large Email Handling allows you to reliably block emails above a defined size, or alternatively, depending on your settings, to store them securely in Retarus’ own datacenters. In the latter case, the recipient is notified by email and may release affected messages individually. The recipient will be informed such an email, should this have been configured. The user may download this email using an HTTP link and simplified authentication (OneClick token login).
Email Signature / Disclaimer
The customer has the opportunity of storing signatures or disclaimers in the Enterprise Administration Services Portal (EAS Portal). Retarus then attaches the signatures or disclaimers created via the EAS Portal to the customer's outbound emails. When using placeholders, these will be replaced with data from Directory Synchronization.
Email Live Search
Email Live Search provides detailed results on the status of individual emails in real time. This search function makes it easier to find emails, simplifies the analysis of delivery delays, and supports IT forensics. For example, the help desk can release emails marked as graymail to users from within user guidance.
Access Management
A customer may assign access permissions for individual administrators according to the customer's requirements via the Retarus Enterprise Administration Services Portal (EAS Portal), e. g. different access permissions for certain countries, branches, domains or departments.
Email Security
Retarus Email Security protects complex email infrastructures from malware like viruses, spam, phishing emails, ransomware and other digital threats. The multi-level filtering methods and data sources are constantly kept up to date and optimized. Data processing takes place in Retarus' own data centers pursuant to the data protection rules currently in force.
AntiVirus Multiscan 2x
Retarus scans incoming and – where agreed – outgoing messages for viruses. To carry out these scans, Retarus uses two virus scanners of their choosing from different providers. As soon as there are updates or releases from these providers, Retarus will use them for virus scans immediately. Should a virus be detected, Retarus deletes any and all emails infected. The respective recipients of the infected emails and/or their administrators saved for such an occasion, will be informed as part of quarantine management.
AntiVirus Multiscan 4-stage
Like AntiVirus Multiscan 2-stage, checking for viruses takes place, but using virus scanners by four different providers.
External Sender Visibility Enhancement
External Sender Visibility Enhancement marks incoming messages that use a sender domain assigned to the customer for sending. For sender validation, the header field 'MIME-FROM' is used. Incoming messages will be marked using pre-defined Unicode icons (symbols) within the Retarus infrastructure, before being transmitted to the customer's infrastructure. Marking takes place in the 'friendly name' sender field.
AntiSpam Management and Phishing Filter (Inbound)
The messages received by Retarus and meant for the customer, will be checked using the respective spam filter utilized by Retarus, assigned a SPAM probability score and identified as 'potential spam' using the customer-specific limits. Those messages identified as 'potential spam' will not be delivered directly but rather treated in quarantine management according to the configuration. Alternatively, messages recognized as SPAM can be marked accordingly and delivered if configured by the customer wishes ('tag and deliver'). Retarus utilizes different filter, pattern, recognition procedures and technologies to achieve this. The phishing filter checks links in incoming emails against special sources for phishing URLs. Recognition and further processing of the messages quarantined are to be carried out by the customer and their defined users.
AntiSpam Management and Phishing Filter (Outbound)
Similar to Retarus AntiSpam Management and Phishing Filter (Inbound), the Outbound counterpart employs the renowned spam filter technology utilized by Retarus. Each outgoing email is assigned a SPAM probability score, and those surpassing a configurable threshold (default set at 60%) are subject to different disposition options based on your configuration preferences. The available choices include rejection, temporary failure (tempfail), or silent discarding, allowing you to tailor the response to align with your specific security policies. The configuration flexibility extends to all hierarchy levels, enabling you to fine-tune settings at the customer, domain, profile, and user levels. To activate the feature, please reach out to the Retarus Support team.
Attachment Blocker
Delivery of certain email attachments may be prohibited according to the customer's configurations. Attachments to be blocked can be selected using data type extensions (e. g. exe, mp3, zip) as well as using the respective MIME types. The file attached to an incoming email will either be deleted and only the email body will be delivered to the recipient, or a copy of the original email including the attachment is sent to a pre-defined mailbox (e. g. administrator). Recipients can be informed about deleted attachments using configurable notifications.
Outbound Recipient Restriction
By default, outgoing emails processed by Retarus may have up to 600 recipient addresses. If an email exceeds this threshold, Retarus rejects it for the exceeding recipients, and notification depends on your email server's configuration. Our Outbound Recipient Restriction feature empowers you to set a custom maximum number of recipients (0-600) for outbound emails. Exceeding the configured limit can trigger rejection, temporary failure, or silent discard based on your preferences. This capability is aimed at limiting recipients, preventing identity exposure, and facilitating efficient administration. The feature may be configured on all hierarchy levels (customer, domain, profile, user). To activate this feature, assistance by the Retarus Support team is initially required.
Outbound Size Restriction
By default, outgoing emails processed by Retarus may have a size up to 250 MB (256000 kB). The “Outbound Size Restriction” feature allows you to restrict the size of outgoing (Outbound) emails even further, if required. Exceeding the configured limit can trigger rejection, temporary failure, or silent discard based on your preferences. The feature may be configured on all hierarchy levels (customer, domain, profile, user). To activate this feature, assistance by the Retarus Support team is initially required.
Deferred Delivery Scan
As part of Deferred Delivery Scan (DDS), specific file attachments are further analyzed using additional re-scan procedures. Using these additional scans with more current signatures, delivery of harmful content which have not been identified during the first scanning, can be prevented at a higher rate. If a virus is found in an email, Retarus deletes the infected email and sends notifications according to the configuration in quarantine management. As DDS leads to delayed delivery of incoming email, potentially-agreed service levels in regard to delivery times may not apply.
Time-of-Click Protection
Links included in emails are automatically re-written (URL Rewriting). If the recipient clicks on the respective links, these will be checked for target addresses, suspected of being involved in phishing. Should the target site not be recognized as phishing, the user will be forwarded directly. Should the target site be a phishing site, a security warning will be displayed. After termination of the service, the respective links may no longer be immediately reachable.
CxO Fraud Detection
CxO Fraud Detection uses algorithms identifying 'From Spoofing' and 'Domain Spoofing', and recognizing fake recipient addresses (e. g. high-ranking superior within company). Messages classified as CxO Fraud will be treated in quarantine management according to the configuration.
Sandboxing
During Sandboxing, specific file attachments are further analyzed. Attachments including potentially harmful content will be executed by a virtual machine and checked for unusual behavior. For these checks, a specialized third-party provider's Sandbox solutions is used. In the case of an infection with harmful content being identified, the respective messages will be treated in quarantine management according to the configuration. Given that Sandboxing etc. may lead to delayed delivery of incoming emails, depending i. a. on file size, file type and number of file attachments, potentially-agreed service levels regarding delivery times may not apply.
Patient Zero Detection®
Patient Zero Detection® creates a digital fingerprint ('Hash') of all file attachments and links during receipt by the email addresses directed to the customer's recipients. Should the virus scanners employed by Retarus detect harmful content in attachments or links at a later time, also recipients of delivered and potentially harmful messages can be identified early on. The customer's administrators and the recipient of the messages, if instructed to do so, will be informed about this immediately. The customer, thus, has the opportunity to take measures to remove the harmful code from their infrastructure or prevent spreading of the harmful code.
Patient Zero Detection® Real-Time Response
Thanks to Patient Zero Detection® Real-Time Response, Retarus can offer software that the customer can operate within their own infrastructure. This software automatically processes messages identified as harmful by Patient Zero Detection® after delivery to the recipient's mailbox. These messages can, then, be deleted from the recipient's mailbox automatically. In order to operate Patient Zero Detection® Real-time Response, using 'Retarus Forensic SIEM Integration' as well as a connection to Microsoft Exchange on the customer's side are necessary. For Patient Zero Detection® Real-time Response, separate terms of use apply, which the customer has to consider and adhere to in the case of installing and using the software. These terms of use can be found in the EAS Portal as well as online.
Quarantine Management
As part of Quarantine Management, the customer, and, if requested by the customer, their individual users, can request delivery of an email security report (Digest) at customizable points in time. The Digest, depending on the requested options, includes a combined overview over emails, which were quarantined or deleted by Retarus based on Graymail (e. g. newsletters), viruses, spam, phishing, Sandboxing, CxO Fraud etc. within the defined time period. Quarantined messages can be accessed by the customer by clicking on the respective entry in the digest within the defined time period (for a maximum of 30 days). Should the customer have so decided, the individual recipients can access their quarantine online and create their own settings. The customer's administrators can configure quarantine settings across the system using the Enterprise Administration Services Portal (EAS Portal).
Forensic SIEM Integration
As part of Forensic SIEM Integration, Retarus provides an interface that the customer can use to request information about events and results (Event, and Log), resulting from in- and outbound messaged within the Retarus Email Security. This can be included into an existing SIEM tool as an additional data source. Events provided for the customer depend on the booked options and are available for:
AntiVirus Multiscan (inbound and outbound)
Sandboxing
CxO Fraud Detection
Patient Zero Detection®
Outbound emails, in general
Inbound emails, in general
Advanced Routing & Rewriting
Advanced Routing & Rewriting allows Retarus to deliver emails for predefined recipients within a domain to a designated destination server. This routing capability can be combined with address rewriting as part of the Predelivery Logic.
Email Compliance
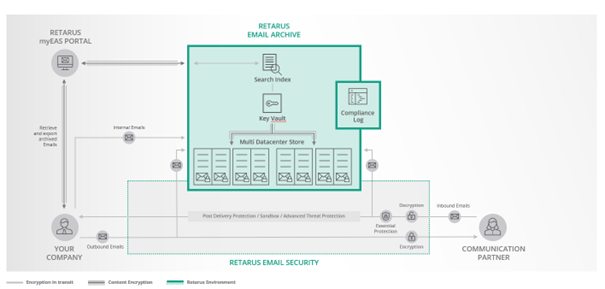
Retarus Email Archive
The Retarus Email Archive stores incoming and outgoing email communication – automatically, reliably and for the long term. If required, internal email communication can also be stored in the Retarus Email Archive.
Messages handed over to the Retarus Email Archive are uneditable, protected from unauthorized access and retrievable. These messages are stored for the term of the agreement, for a maximum of ten years, and will be deleted at the end of the agreed duration in compliance with the law, unless agreed otherwise. During the archiving period, archived emails can be found and re-delivered easily by the customer, using various filtering options. Should the customer wish to export the entire archive before the end of the agreed archiving period and the deletion of the emails, this is to be requested by the customer before the end of the term.
Administrator access to the email archive is based on the dual-control principle. Archived emails and attachments can be found quickly using powerful search functionalities, which can be restricted granularly, if necessary, e.g., in the case of data protection requirements.
A complete access protocol will be created automatically.
Functionalities
Reliable long-term storage of all incoming and outgoing emails
Uneditable, secure data storage based on hybrid encryption
Providing tracking information via EAS Live Search
Access protocol created automatically
Support in meeting regulatory requirements
Messages retrievable incl. attachments
Access based on dual-control principle via the web-based Retarus administrative portal
Powerful search functionality with configuration option for data-protection compliance: Finding emails based on sender, recipient or attachment file format; configurable storage of respective (meta) data for search by subject, full text or attachment name
Options upon request
Archiving of internal email communication via Journaling (Microsoft Exchange or M365 Exchange Online)
Secure and convenient access for customer’s administrators via Single Sign-on
Importing emails from other archiving systems (ideally in eml format)
Exporting archived emails to external data storage
Using customer’s own (public) keys (private keys remain with customer)
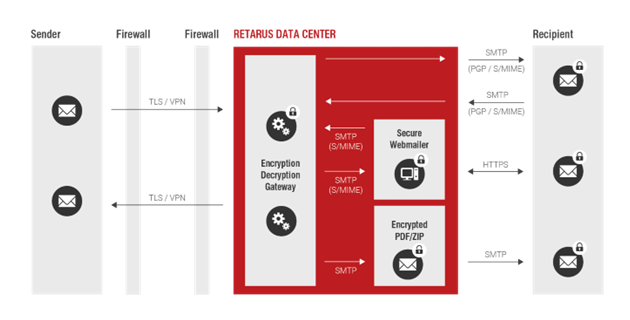
Retarus Email Encryption
Retarus Email Encryption supports the customer to maintain integrity, authenticity and confidentiality of email messages. In order to do so, emails are either encrypted in the Retarus System including their attachment via pre-defined rules or on a user-specific basis, and/or signed on an on-demand basis before sending them to the recipients. A requested check for viruses is carried out before encryption for outgoing emails and after decryption for incoming emails.
Further functionalities
Adopting existing Public Key Infrastructures (PKIs)
Further use of existing and valid S/MIME certificates
Support of Open PGP, PGP and S/MIME standards
Integration of customer’s own encryption policies
Provision of Microsoft Outlook Add-ins for controlling user actions for encryption and/or signature of messages
Provision of alternative encrypted ways of communicating via the Retarus Secure WebMailer or sending of encrypted PDF or ZIP files
Optional integration of an official Trust Center (currently SwissSign) for creating S/MIME certificates according to X.509 standard
Automated user synchronization for creating and renewing certificates (upon request)
System Architecture of Retarus Email Encryption
Initial Email Encryption workshop
The initial Email Encryption workshop is a necessary requirement for configuring Retarus Email Encryption. In this workshop, the customer, together with Retarus, will define customer-specific requirements for setup. Topics may include:
Introduction to cryptography,
Presentation of established standard,
Taking stock of existing infrastructure,
Analysis of customer-specific requirements and security policies,
Definition of workflows and processes, e. g. pertaining to encryption/signature or collecting public keys,
Definition of layouts and contents for email notifications,
Definition for using the Secure WebMailer (e. g. transmission of access data),
Definition for using an encrypted PDF document (e. g. transmission of password).
Based on the results of this workshop, the Retarus sets up customer-specific encryption mandates in the Retarus system, based on the S/MIME and PGP standards or alternative encryption methods (Secure WebMailer / encrypted PDF or ZIP).
User Synchronization for Encryption (USE)
The User Synchronization for Encryption (USE) is a solution that simplifies the management of encryption users, groups and their associated S/MIME or PGP keys. With the focus on improving user experience and reducing the manual intervention, USE automates the renewal, verification and revocation process of certificates and keys by monitoring the expiration dates and initiating the necessary action.
Capable of securely importing encryption users and assigning them to predefined groups.
Manages policies based on customer requirements and user groups.
Automates creation/revocation and synchronization of S/MIME (SwissSign).
Distinguishes between personal and team certificates to avoid disruptions.
Features fully automated recertification or semi-automated recertification.
Creates/deletes PGP keys and synchronizes corresponding private keys for each user.
Allows import of keys/certificates separately created/bought by customers.
Rule notation for administering customer-specific encryption policies in a human-readable way.
Capable of generating sync reports and S/MIME transactional reports for compliance and auditing.
Reports can be received via email or stored on the SFTP share for collection.
Digital Signature / Certificates
Using Retarus Email Encryption, outbound emails can be signed on demand or automatically pursuant to the rules, using PGP keys or S/MIME certificates. For inbound emails, the user can easily see the result of the signature check thanks to transparent information. In addition to S/MIME certificates according to standard X.509 (email certificates of class 2), optional S/MIME certificates of a trust center (currently SwissSign) can be used. Such certificates are provided via the Managed PKI (MPKI). As well as the Retarus terms and conditions, customers are also required to accept the trust center's terms and conditions.
Secure Webmailer
Secure Webmailer is a secure web portal that customers can use to exchange encrypted emails with communication partners who neither use S/MIME nor PGP. To this end, a personal mailbox automatically created in the Retarus Secure WebMailer can be accessed via a link. All access is HTTPS-encrypted. Transmitting personal access data to the respective communication partner as well as optional enterprise-specific design of the Secure WebMailer and the notifications intended for the respective email sender and recipient are defined together with the customer as part of the initial Email Encryption workshop.
Encrypted PDF /ZIP
Retarus offers the opportunity of transmitting confidential information as a password-secured PDF document or a password-secured ZIP file. When doing so, the email text body including all attachments is integrated into a PDF or ZIP file, which is encrypted and then forwarded to the recipient. The transmission of the password for opening the PDF document or ZIP file as well as an optional adaptation of the template used will be taken care of together with the customer in the initial Email Encryption workshop.
Extension for machine- and/or application-generated messages (eBusiness user)
Processing of machine- and/or application-generated messages from fixed automatisms, portal applications or process-linked solutions (e. g. a signature module) takes place via a so-called eBusiness licence). Doing this, each sender address of such an application is assigned to an individual eBusiness user licence. When optionally using S/MIME certificates, Retarus manages class 2 certificates of the 'silver' category on the customer's behalf.
Data Loss Prevention
Data Loss Prevention checks emails from senders on the customer's side to external recipients for patterns defined as part of the configuration, e. g. credit card number or bank account numbers (IBAN). Should an email contain such a pattern, transmission to external recipients is prohibited. Additionally, certain members of staff, e. g. an administrator or a compliance officer, may be informed about such an attempt of sending. The email in question will be attached to the notification. Optionally, the original sender may also be informed. Checking for such patterns includes the email body. Furthermore, sending attachments can be prohibited using file extensions (e. g. exe, mp3, zip) as well as the respective MIME type. Additionally, the customer can specify that emails are only sent to external recipients if a supervisory body, e. g. a functional mailbox, is part of the mailing list.
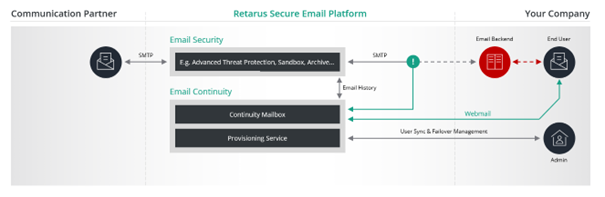
Retarus Email Continuity
Retarus Email Continuity is an alternative email platform for ensuring email communication in disaster scenarios (e. g. malware infiltration, data center malfunction, cloud downtime). If required by the client, the receipt and sending of in- and outbound emails are routed via this platform.
Further functionalities
End-user access to the email continuity mailbox via webmail (HTTPS)
Internal directory functionality for displaying and finding all transmitted contact information within the customer domain concerned.
Administrative access to the Continuity service via REST API for managing continuity mailbox users.
Mailbox setup via the Retarus Directory-Synchronization using a csv file
Automatic notification of newly-added Continuity users
Password self-service via a landing page (via security tokens that the customers manages)
Back-transmissability of emails from the email continuity mailbox (Backsync) to the productive environment.
Optional access to all inbound messages of the last few days (email history of up to 14 days) according to the domains assigned to the customer. For this, a reference to the customer's specific MX records to the Retarus infrastructure are required
System Architecture Retarus Email Continuity
Retarus Predelivery Logic
Using the Retarus Predelivery Logic, the processing of messages within the Retarus infrastructure is influenced, before delivery to the customer's infrastructure.
The customer configuration takes place via creating individual rules in the EAS portal, made of 'conditions' and 'actions'. For example, Routing and rewriting can be done based on certain header information such as sender, user or email subject.
