Configuring a Graph API connection
The sample code requires the following details for executing Microsoft Graph API queries:
Tenant ID
Client ID (Application ID)
Client Secret
Tenant ID
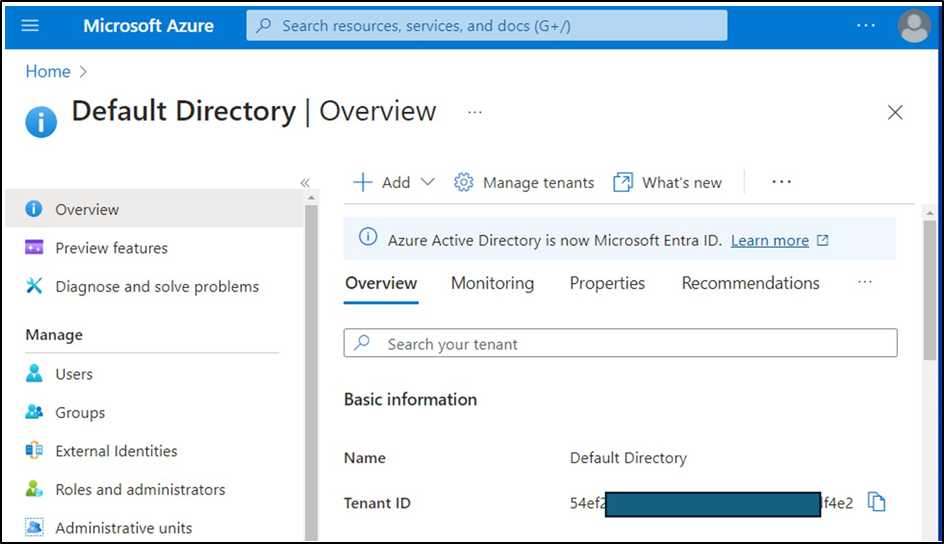
The Tenant ID refers to the unique identifier of your Azure tenant. It can be found under:
Microsoft Entra ID → Overview → Basic Information → Tenant ID
Client ID (Application ID)
The Client ID can be found under Entra ID → Enterprise applications → New application OR <Select your existing application>
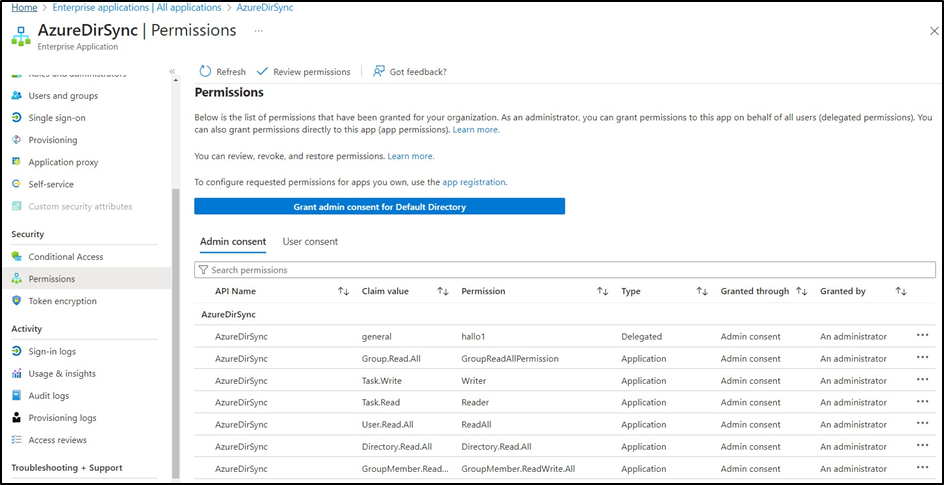
It is necessary to define the required permissions for the enterprise application. Below is an example of possible authorizations when using Microsoft Graph API.
Client Secret
This manual and the provided sample code use the app-only access authentication model, which requires setting up a client secret. It is also possible to use delegated access with custom scopes that do not require a client secret.
For more details on authentication and authorization with Microsoft Graph API, refer to the official Microsoft documentation:
Authentication and authorization basics - Microsoft Graph | Microsoft Learn
The sample code assumes the use of app-only access with a client secret. To configure a client secret:
Navigate to MS Entra ID → App Registrations → <
Select your existing application>.Go to Certificates & secrets → Client secrets.
Customers can decide whether the certificates used for Graph API queries should expire or be valid indefinitely (Custom option).
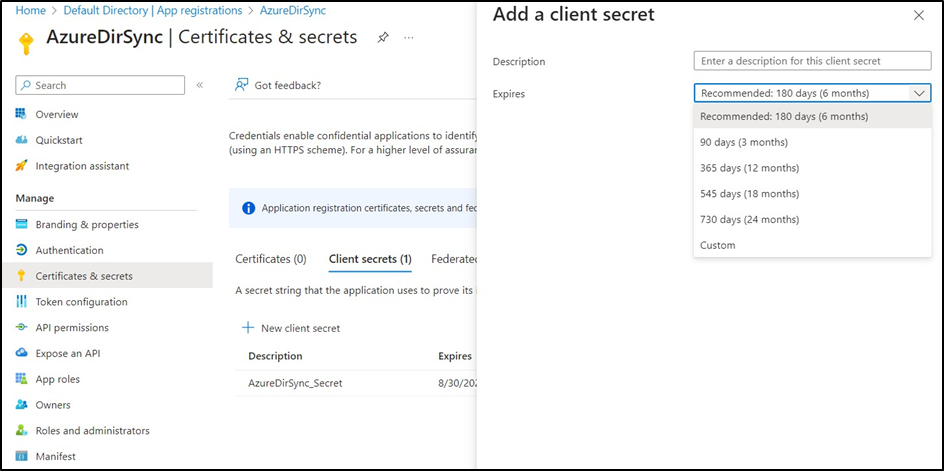
If certificates are set to expire, it is recommended to configure a reminder system for upcoming expirations. One approach is to create an automation account in Microsoft Entra ID with a runbook that executes a PowerShell script to send email notifications about expiring certificates.
For more details, refer to:
How to Receive Email Notifications for Expiring Azure App Registration Certificates and Secrets
Alternatively, you can search the web for:How to Receive Email Notifications for Expiring Azure App Registration Certificates and Secrets
Managing the Entra ID tenant, including certificate expiration and renewal policies, is the customer’s responsibility. These tasks are not part of Retarus' consulting services during onboarding and are not covered by Retarus support for existing customers.
Resource groups
A resource group must be created to manage the Azure Function and the blobStorage object.
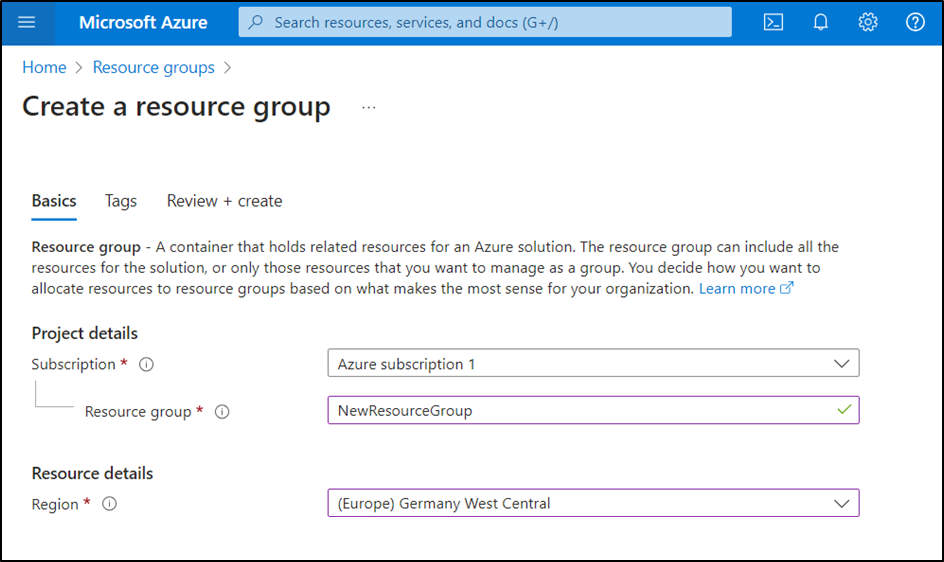
The resource group requires:
A function app
A storage account (which stores
m2f.csv,f2m.csv, and intermediate CSV files whenmode[1,2]_multiRecipients=true)
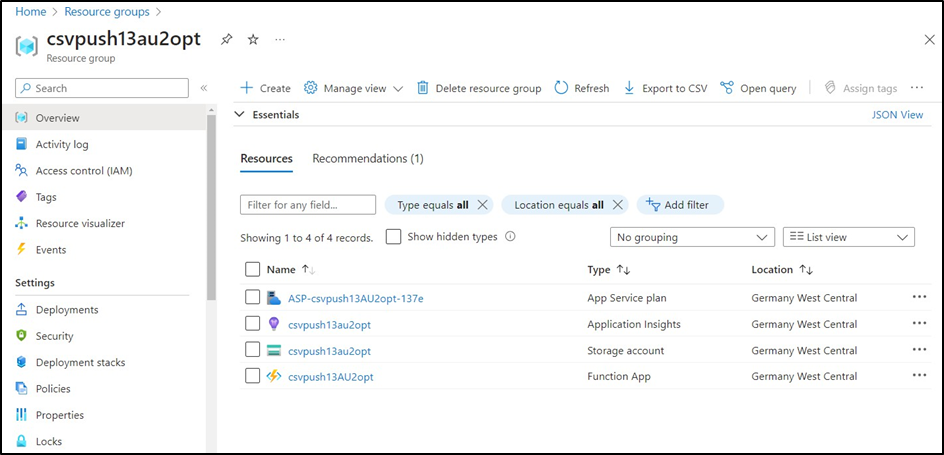
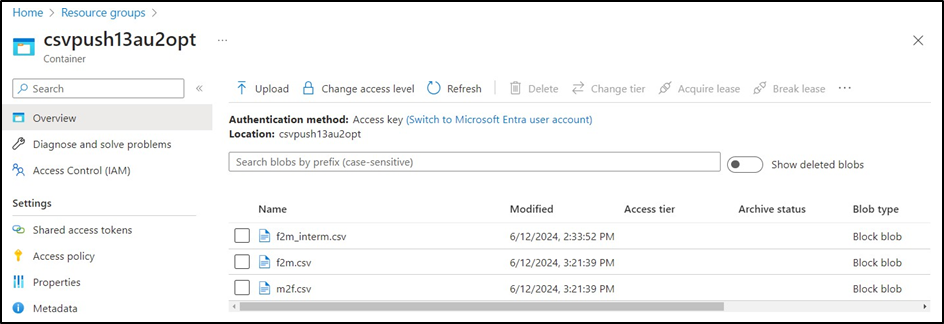
The files will be stored in:
Storage account → Data storage → Containers → <Select the container>
The image below displays an intermediate .csv file (see mode1_multiRecipients and mode2_multiRecipients for details), along with the m2f.csv and f2m.csv files. Only m2f.csv and/or f2m.csv are pushed to Retarus.